Dozens of Android camera applications, some of them with over 1 million installs on the Google Play Store, were serving malicious ads and fake update prompts while also making sure that they won't be uninstalled by hiding their entries from the application list.
Lorin Wu, a mobile threats analyst for Trend Micro, sorted these malicious apps in two different categories: some of them were variations of the same camera application designed to beautify photos, while the other kind allowed their users to apply photo filters on their snapshots.
These apps have all been removed from the Google Play store by now, but not before they were able to amass millions of installations (some of them most probably fake).
All of them were also obviously connected to each other given that they were sharing various design components such as the screenshots added to their Google Play entries.
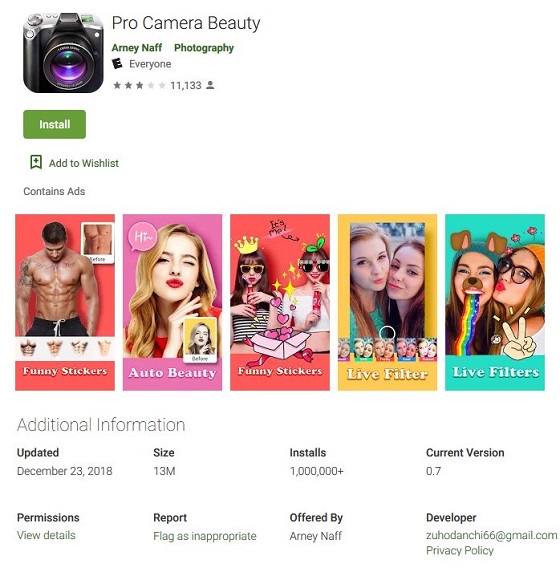 Malicious app's Google Play entry
Malicious app's Google Play entryAccording to Wu, the beauty camera apps detected as AndroidOS_BadCamera.HRX, were "capable of accessing remote ad configuration servers that can be used for malicious purposes."
After installation, they would automatically hide from the application list to make sure the victim would not be able to remove them and start displaying adult content and fraudulent content ads using the default web browser after every device unlock event.
To add insult to injury, the user would not be able to pinpoint the app that pushed the ads, while some of the advertisements redirected the victims to websites which asked for personal information to be able to collect various fake prizes.
The ads were displayed using ad configurations downloaded in JSON format which also contained instructions designed to allow the apps to adjust the ad behavior depending on the compromised device.
 Malicious ad pop-ups
Malicious ad pop-upsThe other batch of malicious Android applications which targeted users who wanted to apply filters to their selfies could be considered even more dangerous considering that they uploaded their victims' snapshots to servers their authors controlled.
Seeing that none of them actually worked as advertised, only delivered fake update screens, and also hid themselves to avoid being uninstalled, their authors' intent was clearly malicious.
 Fake update screens
Fake update screensAs
TrendMicro states, "The authors can collect the photos uploaded in the app, and possibly use them for malicious purposes — for example as fake profile pics in social media."
Scores of malicious apps also installed by millions of users have been previously found on the Google Play store, stealing banking information while trying to avoid detection with the help of the motion sensor, showing ads while impersonating GPS apps and a host of other Android utilities.
source