Cobalt Dickens, a threat actor associated with the Iranian government, ran a phishing operation in July and August that targeted more than 60 universities in countries on four continents.
Security researchers say that the group's hacking activity affected at least 380 universities in more than 30 countries, many of the targets being hit multiple times.
Free domains and TLS certsThe latest phishing campaign was directed at organizations in Australia, Hong Kong, the U.S., Canada, the U.K., and Switzerland. It used at least 20 new domain names registered using the Freenom service that offers free top-level domain names (.ml, .ga, .cf, .gq, .tk).
A fraudulent email Cobalt Dickens sent to people with access to the library of the targeted university, shows a message that prompted to reactivate the account by following a spoofed link.
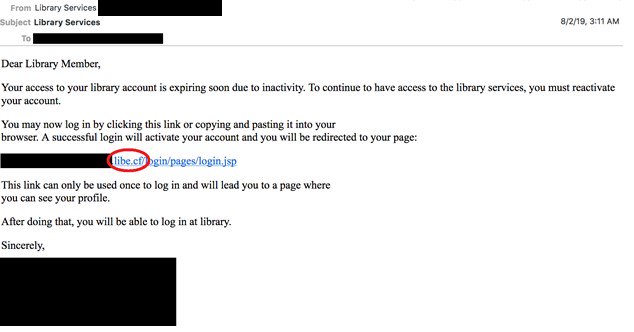
Using a spoofed link is a change in the modus operandi as previous campaigns from the group relied on shortened URLs to direct to the fake login page.
Following the fake link leads "to a web page that looks identical or similar to the spoofed library resource," say researchers from Secureworks' Counter Threat Unit (CTU).
Once the credentials are provided, they are stored in a file named 'pass.txt' and the browser loads the genuine university website.
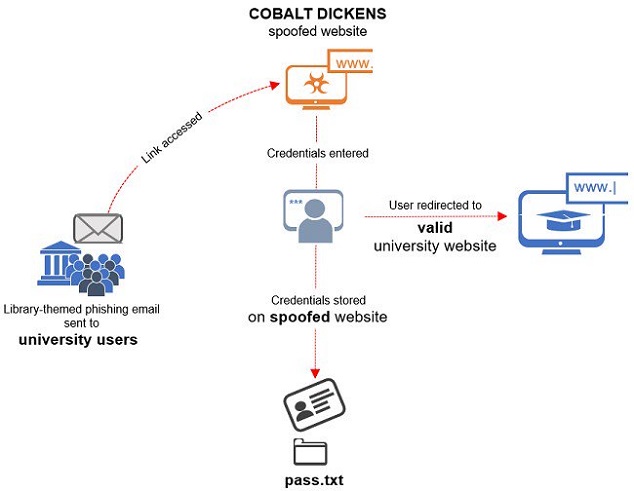
To cancel suspicions of fraudulent activity, the threat actor often uses valid TLS certificates for its websites. Most of the certificates observed in this campaign are free, issued by the Let's Encrypt non-profit certificate authority.
Unconcerned by public exposureAlso known as Silent Librarian, the group focuses on compromising educational institutions, although its victims count private sector companies, too. Its purpose seems to be stealing library account credentials and selling academic resources as well as access to them to customers in Iran.
Nine individuals believed to have roles in the group's activity were indicted by the US Department of Justice in March 2018 for cyber intrusion activities. It is believed that they were partners or hacker-for-hire for a company called Mabna Institute that carried hacking operations since at least 2013.
Many of the intrusions were allegedly committed for the Islamic Revolutionary Guard Corps (IRGC), an entity in the government charged with collecting intelligence.
Their targets were "computer systems belonging to 144 U.S. universities, 176 universities across 21 foreign countries, 47 domestic and foreign private sector companies."
The list of targets also includes the U.S. Department of Labor, the Federal Energy Regulatory Commission, the State of Hawaii, the State of Indiana, the United Nations, and the United Nations Children’s Fund.
It is alleged that the hackers stole more than 31 terabytes of documents and data from victims across the globe. However, despite the indictment in the U.S. and public exposure, Cobalt Dickens seems to be undeterred in its operations.
In an effort to put the brakes on the threat actor's operations, Secureworks published all known domains associated with Cobalt Dickens.
source