21
Huawei / Huawei and OrangePi launch new dev board with mystery CPU and AI processor
« Last post by javajolt on May 12, 2024, 06:19:23 PM »Huawei again hides chip specs from prying eyes
Quad-core mystery chip with an in-built AI accelerator emerges.

(Image credit: OrangePi)
Huawei and OrangePi have announced a joint venture in the OrangePi Kunpeng Pro development board. The Raspberry Pi alternative runs not only a quad-core 64-bit Arm processor but also an AI processor that's integrated into the same package, but Huawei and OrangePi aren't releasing the specifics of the processor. In fact, the name of the chip has been hidden in the official renders, a practice that we've seen from Huawei in the past as it seeks to avoid prying Western eyes. However, we dug into the documentation to confirm that the chip is based on a custom Huawei Kunpeng CPU design. It features new tech that we haven't seen from Kunpeng processors before, showing that Huawei's Kunpeng line of chips is advancing into the AI realm.
The single-board computer includes tools and capabilities suitable for consumers, developers, and students. It comes with the [color-blue]openEuler OS[/color] preinstalled, along with the openGauss database and a suite of internet, productivity, and software development packages.

The OrangePi Kunpeng Pro development board (Image credit: OrangePi)
The Kunpeng Pro development board uses a custom Huawei Kunpeng CPU that's paired with an AI FPGA processor. Huawei has been under severe sanctions from the U.S. government, limiting its access to certain chips and chip-making technologies. Therefore, OrangePi and Huawei aren't revealing the specific model number of the Kunpeng CPU, but we do know that it is a quad-core ARM model.
Both the CPU and FPGA are placed in the same chip package, but it isn't clear if the CPU and FPGA are separate chiplets under the same heatspreader or if they are integrated onto the same die. Regardless of whether the FPGA and CPU reside on chiplets or the same die, this represents a new capability for Huawei's custom Kunpeng chip designs.
The AI processor provides 8 TOPS of AI computing power. For the sake of comparison, the Qualcomm Snapdragon X Elite and Apple M4 neural engines are rated for 45 TOPS and 38 TOPS, respectively. OrangePi and Huawei have equipped the Kunpeng Pro development board with two HDMI ports supporting 4K displays, a Type-C power interface, Wi-Fi 5, and Gigabit Ethernet.
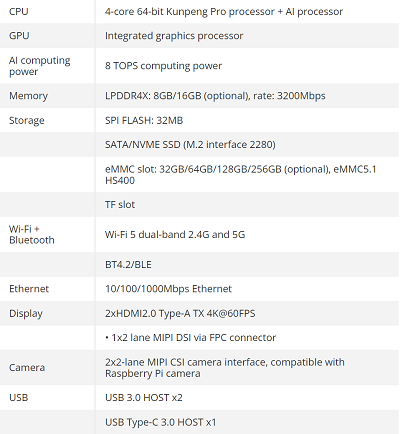
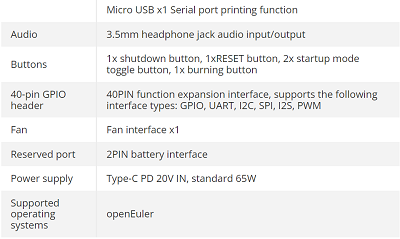
The full specifications are:
OrangePi Kunpeng Pro is available only through Chinese retailers at this time. Pricing starts at 1,076 yuan (approximately $148.92 USD.) IT Home lists four available packages of the OrangePi Kunpeng Pro.

source
Quad-core mystery chip with an in-built AI accelerator emerges.

(Image credit: OrangePi)
Huawei and OrangePi have announced a joint venture in the OrangePi Kunpeng Pro development board. The Raspberry Pi alternative runs not only a quad-core 64-bit Arm processor but also an AI processor that's integrated into the same package, but Huawei and OrangePi aren't releasing the specifics of the processor. In fact, the name of the chip has been hidden in the official renders, a practice that we've seen from Huawei in the past as it seeks to avoid prying Western eyes. However, we dug into the documentation to confirm that the chip is based on a custom Huawei Kunpeng CPU design. It features new tech that we haven't seen from Kunpeng processors before, showing that Huawei's Kunpeng line of chips is advancing into the AI realm.
The single-board computer includes tools and capabilities suitable for consumers, developers, and students. It comes with the [color-blue]openEuler OS[/color] preinstalled, along with the openGauss database and a suite of internet, productivity, and software development packages.

The OrangePi Kunpeng Pro development board (Image credit: OrangePi)
The Kunpeng Pro development board uses a custom Huawei Kunpeng CPU that's paired with an AI FPGA processor. Huawei has been under severe sanctions from the U.S. government, limiting its access to certain chips and chip-making technologies. Therefore, OrangePi and Huawei aren't revealing the specific model number of the Kunpeng CPU, but we do know that it is a quad-core ARM model.
Both the CPU and FPGA are placed in the same chip package, but it isn't clear if the CPU and FPGA are separate chiplets under the same heatspreader or if they are integrated onto the same die. Regardless of whether the FPGA and CPU reside on chiplets or the same die, this represents a new capability for Huawei's custom Kunpeng chip designs.
The AI processor provides 8 TOPS of AI computing power. For the sake of comparison, the Qualcomm Snapdragon X Elite and Apple M4 neural engines are rated for 45 TOPS and 38 TOPS, respectively. OrangePi and Huawei have equipped the Kunpeng Pro development board with two HDMI ports supporting 4K displays, a Type-C power interface, Wi-Fi 5, and Gigabit Ethernet.
The full specifications are:


OrangePi Kunpeng Pro is available only through Chinese retailers at this time. Pricing starts at 1,076 yuan (approximately $148.92 USD.) IT Home lists four available packages of the OrangePi Kunpeng Pro.

source

 Recent Posts
Recent Posts