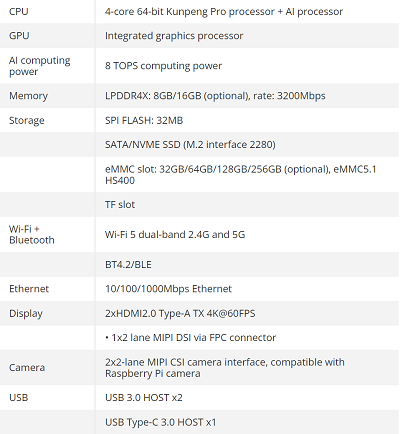
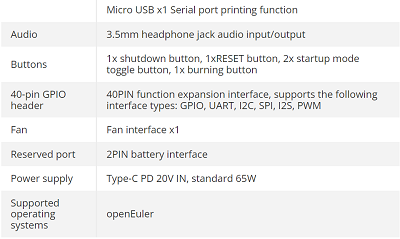
11
Windows 10 Help | How To & Fixes | Tips & Tricks / How to clean the dust out of your PC tower
« Last post by javajolt on May 15, 2024, 05:19:39 AM »Dust buildup is bad for your system, so you should regularly clean your PC tower to keep it free of dirt and grime

Cleaning is a crucial part of the PC maintenance routine, and we can't stress how important it is to regularly dust and clean your PC tower. If you ever peek inside your PC's chassis, and you see piles of dust gathered around the internals, then that's not a good sign. We say that because the dust and grime that's collecting on your PC's power and its internals are not only tarnishing its looks, but they're also significantly affecting your PC's performance by reducing the thermal efficiency of your system.
Even the best PC cases will eventually accumulate enough dust to start impacting your system's performance, so it's important to ensure you're getting rid of the dust frequently. While the process of cleaning your PC tower may sound rather tedious, this step-by-step procedure will help you selectively clean the components that are prone to collecting a lot of dust during everyday usage.
What you’ll need
The prerequisites
Most PC cases use thumbscrews to keep the front and back panels in place, but you’ll need a Phillips screwdriver if you plan to unmount the components during the cleanup procedure.
As for the cleaning tools, you’ll need a can of compressed air to get rid of all the dust and debris on your components. Additionally, you’ll need some isopropyl alcohol wipes to properly clean the non-fragile PC parts. You can technically use rubbing alcohol, but I would advise against it as rubbing alcohol contains more traces of water, which can harm your PC's internals. As such, you should typically use isopropyl alcohol with over 90% alcohol concentration when you clean your PC.
Before you begin
Prepare your PC for a clean-up
There are certain steps you should take to ensure that you don't harm yourself or your PC during the cleanup procedure.
1. Turn off your PC and unplug all the cables connected to it.
2. Press and hold the power button for at least 20 seconds to drain all residual power from the PSU.
3. Move the PC tower to a well-ventilated area to ensure that the dust does not settle back into your rig after you finish cleaning it.
4. Remove the front and side panels after loosening the thumb screws that hold them in place.
How to clean the dust out of your PC tower
A step-by-step guide
Cleaning your PC is a lot easier than you think because dust tends to gather around the fans and on the surface of the components instead of settling inside the parts. The most dust-attracting components of your PC are the dust filters, cabinet fans, GPU fans, and the CPU cooler, so you should focus on these parts during the cleanup procedure.
1. Start by removing the dust filters from your cabinet and cleaning them with isopropyl alcohol wipes.

2. Use a compressed air duster to get rid of the dirt and dust accumulated on the case fans. Alternatively, you can use a microfiber cloth to gently clean them, but you'd want to detach them from the cabinet to avoid damaging them.

3. Next up is the GPU. While you can remove most of the dust from your GPU by simply blowing air on it using a compressed air duster, I’d recommend removing the GPU from the case for thorough cleaning. Detach the PSU wires from the GPU, loosen the expansion slot screws securing it in place, and gently unmount the GPU while pressing down on the PCIe latch.
4. Using a finger or a toothpick, hold the GPU fans in place while you clean them with the compressed air can.

5. If the RAM sticks have some dirt gathered around them, you can blow it away using the compressed air duster.
6. If you want to properly clean the dust off your CPU's cooler, you’ll have to detach the fan from the heat sink. Some CPU fans are attached to the heatsink via latches, allowing you to easily disconnect them, while others require you to unmount the entire cooler from the CPU before you can separate the fan from the heatsink. Consult its manual before going ahead with the unmounting process. Use the same procedure you followed when cleaning the GPU fans to dislodge dirt and grime from the CPU fan and heatsink.
It only takes a few minutes to clean the PC tower regularly

Although your PC is now dust-free, you’ll notice that it’s left in a disassembled state. Once you’re done putting your rig back together, be sure to regularly clean the dust filters every other week and the cabinet fans every three months to prevent dust from gathering inside your PC tower. Cleaning them every once in a while will also help improve your system temperatures.
If you want to improve your PC's thermal efficiency even further, consider looking into the cases with the best airflow. You may be inclined to believe that more airflow is synonymous with increased dust accumulation, but many of these cabinets have dust filters around the intake fans to ensure they don't get clogged with dirt.
source

Cleaning is a crucial part of the PC maintenance routine, and we can't stress how important it is to regularly dust and clean your PC tower. If you ever peek inside your PC's chassis, and you see piles of dust gathered around the internals, then that's not a good sign. We say that because the dust and grime that's collecting on your PC's power and its internals are not only tarnishing its looks, but they're also significantly affecting your PC's performance by reducing the thermal efficiency of your system.
Even the best PC cases will eventually accumulate enough dust to start impacting your system's performance, so it's important to ensure you're getting rid of the dust frequently. While the process of cleaning your PC tower may sound rather tedious, this step-by-step procedure will help you selectively clean the components that are prone to collecting a lot of dust during everyday usage.
What you’ll need
The prerequisites
Most PC cases use thumbscrews to keep the front and back panels in place, but you’ll need a Phillips screwdriver if you plan to unmount the components during the cleanup procedure.
As for the cleaning tools, you’ll need a can of compressed air to get rid of all the dust and debris on your components. Additionally, you’ll need some isopropyl alcohol wipes to properly clean the non-fragile PC parts. You can technically use rubbing alcohol, but I would advise against it as rubbing alcohol contains more traces of water, which can harm your PC's internals. As such, you should typically use isopropyl alcohol with over 90% alcohol concentration when you clean your PC.
Before you begin
Prepare your PC for a clean-up
There are certain steps you should take to ensure that you don't harm yourself or your PC during the cleanup procedure.
1. Turn off your PC and unplug all the cables connected to it.
2. Press and hold the power button for at least 20 seconds to drain all residual power from the PSU.
3. Move the PC tower to a well-ventilated area to ensure that the dust does not settle back into your rig after you finish cleaning it.
4. Remove the front and side panels after loosening the thumb screws that hold them in place.
How to clean the dust out of your PC tower
A step-by-step guide
Cleaning your PC is a lot easier than you think because dust tends to gather around the fans and on the surface of the components instead of settling inside the parts. The most dust-attracting components of your PC are the dust filters, cabinet fans, GPU fans, and the CPU cooler, so you should focus on these parts during the cleanup procedure.
1. Start by removing the dust filters from your cabinet and cleaning them with isopropyl alcohol wipes.

2. Use a compressed air duster to get rid of the dirt and dust accumulated on the case fans. Alternatively, you can use a microfiber cloth to gently clean them, but you'd want to detach them from the cabinet to avoid damaging them.

3. Next up is the GPU. While you can remove most of the dust from your GPU by simply blowing air on it using a compressed air duster, I’d recommend removing the GPU from the case for thorough cleaning. Detach the PSU wires from the GPU, loosen the expansion slot screws securing it in place, and gently unmount the GPU while pressing down on the PCIe latch.
4. Using a finger or a toothpick, hold the GPU fans in place while you clean them with the compressed air can.

5. If the RAM sticks have some dirt gathered around them, you can blow it away using the compressed air duster.
6. If you want to properly clean the dust off your CPU's cooler, you’ll have to detach the fan from the heat sink. Some CPU fans are attached to the heatsink via latches, allowing you to easily disconnect them, while others require you to unmount the entire cooler from the CPU before you can separate the fan from the heatsink. Consult its manual before going ahead with the unmounting process. Use the same procedure you followed when cleaning the GPU fans to dislodge dirt and grime from the CPU fan and heatsink.
It only takes a few minutes to clean the PC tower regularly

Although your PC is now dust-free, you’ll notice that it’s left in a disassembled state. Once you’re done putting your rig back together, be sure to regularly clean the dust filters every other week and the cabinet fans every three months to prevent dust from gathering inside your PC tower. Cleaning them every once in a while will also help improve your system temperatures.
If you want to improve your PC's thermal efficiency even further, consider looking into the cases with the best airflow. You may be inclined to believe that more airflow is synonymous with increased dust accumulation, but many of these cabinets have dust filters around the intake fans to ensure they don't get clogged with dirt.
source

 Recent Posts
Recent Posts