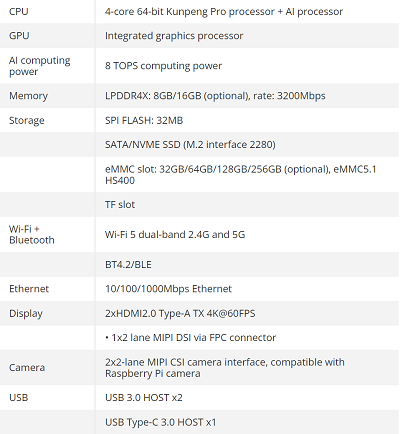
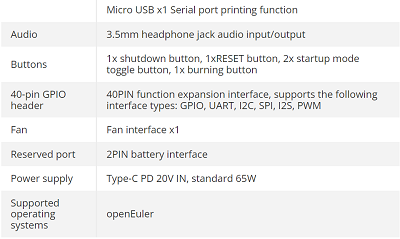
1
Android O.S | Apps / An awesome Android audio upgrade
« Last post by javajolt on Today at 07:26:42 PM »Whether you're dealing with mumblings from meetings, noises from notifications, or music from commute-time streaming, you've never experienced sound on your phone like this.

CREDIT: JR RAPHAEL/GOOGLE/BRONEARTULM
Every now and then, I come across an Android customization concept so clever, so cool, so splendidly useful that I just can’t wait to share it with you.
Today, my fellow Android-appreciating animal, is one of those days.
The concept in question is a hefty and exceptionally practical upgrade for your Android audio experience. It brings a boost to the way you interact with sound on whatever Android device you’re using, no matter who made it or how old it may be. And it’ll take you less than a minute to get going (though, if you enjoy geeking out over details as much as I do, you may find yourself fine-tuning its setup and exploring advanced options within it for a while beyond that).
I’m tellin’ ya: It’s one heck of an improvement. And unlike most of the stuff we’re bound to hear about at Google’s grand I/O gala next Tuesday, it’s something you can start using this very second — and something with an impact that’ll be immediately obvious and genuinely advantageous all throughout your day, both for professional work-related purposes and for any after-hours audio adventuring.
Ready for a whole new level of Android aural pleasure?
Meet your Android audio enhancement
The upgrade of which we speak may seem simple on the surface, but don’t be fooled: This nifty little lift will affect all aspects of your Android-using experience and make your life easier — even saving you time and increasing your efficiency — countless times a day.
It’s a completely new take on the Android volume panel — y’know, the little slider that shows up whenever you tap your phone’s physical volume keys. Unless you’re a complete and total nerd (hello!), that’s probably a part of the Android interface you haven’t spent much time thinking about. But believe you me, once you see how much of a meaningful difference this improvement introduces, you’ll wonder how you went so long without it.
Our upgrade comes by way of a thoughtfully crafted app called Precise Volume 2.0. The app essentially replaces your standard volume panel interface with a totally different, much more customizable, and delightfully feature-rich alternative. (And, yes, you’d better believe this is another one of those wonderful control-claiming superpowers that’d be possible only on Android.)
But enough with the broad blathering. Precise Volume has six especially noteworthy benefits that I’d encourage you to consider:
1. It empowers you to create all sorts of custom presets — specific sets of volume levels for media, ring and notification noises, call and alarm chimes, and even general system sounds — and then activate those with a single swift tap right from your regular volume panel pop-up.
2. It includes easy options for automation, too, so you can instantly have your phone change its volume settings in any specific way anytime a particular app is opened, anytime a specific Bluetooth or wired device is connected, or even anytime a certain day and time arrives.
3. It expands the standard system volume sliders to make ’em much more precise, with a visible zero to 100 scale that lets you get super-nuanced about the exact volume level you want for any given moment or purpose. You can even increase that scale, if you want extra control beyond that, and make your volume sliders operate on a zero to 1,000 step increment setup (or any other measure you like).
4. It includes simple equalizer settings, which can make any audio you’re hearing sound noticeably better and can also be included in those presets and automations we just went over. These settings can even make your phone’s maximum volume higher, if you find things are occasionally too quiet.
5. It adds in a not-yet-broadly-available Android-15-style volume panel expansion that makes all your audio controls even easier to manage from anywhere.
6. And it brings that simple, standard Android design into the volume panel on any device — delivering quite an improvement over the murky mess present on phones by Samsung and other heavy-handed companies by default.

THE PRECISE VOLUME PANEL IN ITS INITIAL FORM, AT LEFT, AND FULLY EXPANDED, AT RIGHT.
Credit: JR RAPHAEL, IDG
Not bad, right? Now, there is one catch: For the full set of features, including the volume panel replacement, you’ll have to pony up six bucks as an in-app purchase for Precise Volume’s Pro version. But you can play around with some of the features even in the app’s free version. And if you like what you find, you’ll likely find that one-time purchase to be very worth its weight.
So let’s get started, shall we?
60 seconds to smarter Android audio
First things first, on the simplest possible level:
• Download Precise Volume 2.0 from the Play Store.
• Open it up and accept the couple of permissions it requests. (They’re completely innocuous and required for parts of the app’s operation.)
• Explore the app’s tabs and the options within ’em to play around with the presets and other features.
For the full-fledged volume replacement panel at the heart of this conversation, meanwhile:
• Tap the Settings tab at the bottom of the Precise Volume interface.
• Tap “Volume Button Override.”
• Flip the toggle next to “Enabled,” then follow the prompts to upgrade to the app’s Pro version.
• Once that’s done, tap that toggle again, then follow the prompt to allow Precise Volume the ability to display itself over other apps. That’s needed for reasons that should be obvious, and there’s no harm in allowing it.
• Once that’s done, tap that toggle one more time — and this time, follow the prompt to enable the app as an Android accessibility service. That may sound scary, but it’s genuinely required for an app to be able to process your physical button presses in this way and effectively replace a part of the system interface. And Precise Volume is extremely up front about the exact reasons for all of its permission requirements and the fact that it doesn’t collect, store, or share any form of personal data.
• After you select the app’s name, be sure to flip the topmost toggle to turn its accessibility service on — not the lower toggle
to activate it as an accessibility shortcut.
• And note that on a Samsung phone, this part of the process is unnecessarily convoluted. After selecting the option to
enable the accessibility service, you’ll have to tap “Installed apps” and then find Precise Volume 2.0 in the list before you’ll
see the relevant option.
And that’s it! Just head back to your home screen and then press your phone’s physical volume-up or volume-down key, and you should see the new Precise Volume panel appear in place of the standard volume pop-up. You can then get to the expanded bottom-of-screen interface by tapping the three dot icon within the regular side-of-screen panel.

THE PRECISE VOLUME PANEL IN ACTION — FROM ZERO TO 100. Credit: JR RAPHAEL, IDG
Beyond that, you’ll absolutely want to spend a bit of time in the “Manage Volume Presets” area of Precise Volume’s Settings tab. That’s where you can create those one-tap presets we talked about a minute ago.

PRECISE VOLUME’S PRESETS MAKE IT POSSIBLE TO CREATE COMPLETE AUDIO SETTINGS FOR ANY
SPECIFIC SCENARIO.
JR RAPHAEL, IDG
The “Automation” area of that same tab is where you can configure simple automations for what happens when specific apps are opened, specific devices are connected, or specific days and times occur — if, say, you want your media volume to bump up and your notification volume to go all the way down whenever you open Google Meet or maybe your notification and ring volume to bump up during the workday but then drop back down in the evenings.

PRECISE VOLUME’S AUTOMATIONS OPEN THE DOOR TO ALL SORTS OF STEP-SAVING SMARTNESS.
Credit: JR RAPHAEL, IDG
The “Behavior” section within that same tab is where you can control the precise nuance level of your volume slider, if you want to make the control even finer than the default zero to 100 scale.

MAKE YOUR VOLUME CONTROL AS NUANCED AS YOU WANT WITH PRECISE VOLUME’S “STEPS” SETTING.
Credit: JR RAPHAEL, IDG
And the Equalizer tab at the bottom of the Precise Volume app is the place where — well, y’know. All that equalizer stuff, including the volume booster, resides.

IT MAY SOUND TECHNICAL, BUT PRECISE VOLUME’S EQUALIZER AREA IS FULL OF SIMPLE,
EFFECTIVE ENHANCEMENTS. Credit: JR RAPHAEL, IDG
And there ya have it: an awesome Android audio upgrade. The power is now at your fingertips, and a smarter, more efficient, and more powerful way of interacting with audio on your phone will always be present and waiting to be called into action.
source

CREDIT: JR RAPHAEL/GOOGLE/BRONEARTULM
Every now and then, I come across an Android customization concept so clever, so cool, so splendidly useful that I just can’t wait to share it with you.
Today, my fellow Android-appreciating animal, is one of those days.
The concept in question is a hefty and exceptionally practical upgrade for your Android audio experience. It brings a boost to the way you interact with sound on whatever Android device you’re using, no matter who made it or how old it may be. And it’ll take you less than a minute to get going (though, if you enjoy geeking out over details as much as I do, you may find yourself fine-tuning its setup and exploring advanced options within it for a while beyond that).
I’m tellin’ ya: It’s one heck of an improvement. And unlike most of the stuff we’re bound to hear about at Google’s grand I/O gala next Tuesday, it’s something you can start using this very second — and something with an impact that’ll be immediately obvious and genuinely advantageous all throughout your day, both for professional work-related purposes and for any after-hours audio adventuring.
Ready for a whole new level of Android aural pleasure?
Meet your Android audio enhancement
The upgrade of which we speak may seem simple on the surface, but don’t be fooled: This nifty little lift will affect all aspects of your Android-using experience and make your life easier — even saving you time and increasing your efficiency — countless times a day.
It’s a completely new take on the Android volume panel — y’know, the little slider that shows up whenever you tap your phone’s physical volume keys. Unless you’re a complete and total nerd (hello!), that’s probably a part of the Android interface you haven’t spent much time thinking about. But believe you me, once you see how much of a meaningful difference this improvement introduces, you’ll wonder how you went so long without it.
Our upgrade comes by way of a thoughtfully crafted app called Precise Volume 2.0. The app essentially replaces your standard volume panel interface with a totally different, much more customizable, and delightfully feature-rich alternative. (And, yes, you’d better believe this is another one of those wonderful control-claiming superpowers that’d be possible only on Android.)
But enough with the broad blathering. Precise Volume has six especially noteworthy benefits that I’d encourage you to consider:
1. It empowers you to create all sorts of custom presets — specific sets of volume levels for media, ring and notification noises, call and alarm chimes, and even general system sounds — and then activate those with a single swift tap right from your regular volume panel pop-up.
2. It includes easy options for automation, too, so you can instantly have your phone change its volume settings in any specific way anytime a particular app is opened, anytime a specific Bluetooth or wired device is connected, or even anytime a certain day and time arrives.
3. It expands the standard system volume sliders to make ’em much more precise, with a visible zero to 100 scale that lets you get super-nuanced about the exact volume level you want for any given moment or purpose. You can even increase that scale, if you want extra control beyond that, and make your volume sliders operate on a zero to 1,000 step increment setup (or any other measure you like).
4. It includes simple equalizer settings, which can make any audio you’re hearing sound noticeably better and can also be included in those presets and automations we just went over. These settings can even make your phone’s maximum volume higher, if you find things are occasionally too quiet.
5. It adds in a not-yet-broadly-available Android-15-style volume panel expansion that makes all your audio controls even easier to manage from anywhere.
6. And it brings that simple, standard Android design into the volume panel on any device — delivering quite an improvement over the murky mess present on phones by Samsung and other heavy-handed companies by default.

THE PRECISE VOLUME PANEL IN ITS INITIAL FORM, AT LEFT, AND FULLY EXPANDED, AT RIGHT.
Credit: JR RAPHAEL, IDG
Not bad, right? Now, there is one catch: For the full set of features, including the volume panel replacement, you’ll have to pony up six bucks as an in-app purchase for Precise Volume’s Pro version. But you can play around with some of the features even in the app’s free version. And if you like what you find, you’ll likely find that one-time purchase to be very worth its weight.
So let’s get started, shall we?
60 seconds to smarter Android audio
First things first, on the simplest possible level:
• Download Precise Volume 2.0 from the Play Store.
• Open it up and accept the couple of permissions it requests. (They’re completely innocuous and required for parts of the app’s operation.)
• Explore the app’s tabs and the options within ’em to play around with the presets and other features.
For the full-fledged volume replacement panel at the heart of this conversation, meanwhile:
• Tap the Settings tab at the bottom of the Precise Volume interface.
• Tap “Volume Button Override.”
• Flip the toggle next to “Enabled,” then follow the prompts to upgrade to the app’s Pro version.
• Once that’s done, tap that toggle again, then follow the prompt to allow Precise Volume the ability to display itself over other apps. That’s needed for reasons that should be obvious, and there’s no harm in allowing it.
• Once that’s done, tap that toggle one more time — and this time, follow the prompt to enable the app as an Android accessibility service. That may sound scary, but it’s genuinely required for an app to be able to process your physical button presses in this way and effectively replace a part of the system interface. And Precise Volume is extremely up front about the exact reasons for all of its permission requirements and the fact that it doesn’t collect, store, or share any form of personal data.
• After you select the app’s name, be sure to flip the topmost toggle to turn its accessibility service on — not the lower toggle
to activate it as an accessibility shortcut.
• And note that on a Samsung phone, this part of the process is unnecessarily convoluted. After selecting the option to
enable the accessibility service, you’ll have to tap “Installed apps” and then find Precise Volume 2.0 in the list before you’ll
see the relevant option.
And that’s it! Just head back to your home screen and then press your phone’s physical volume-up or volume-down key, and you should see the new Precise Volume panel appear in place of the standard volume pop-up. You can then get to the expanded bottom-of-screen interface by tapping the three dot icon within the regular side-of-screen panel.

THE PRECISE VOLUME PANEL IN ACTION — FROM ZERO TO 100. Credit: JR RAPHAEL, IDG
Beyond that, you’ll absolutely want to spend a bit of time in the “Manage Volume Presets” area of Precise Volume’s Settings tab. That’s where you can create those one-tap presets we talked about a minute ago.

PRECISE VOLUME’S PRESETS MAKE IT POSSIBLE TO CREATE COMPLETE AUDIO SETTINGS FOR ANY
SPECIFIC SCENARIO.
JR RAPHAEL, IDG
The “Automation” area of that same tab is where you can configure simple automations for what happens when specific apps are opened, specific devices are connected, or specific days and times occur — if, say, you want your media volume to bump up and your notification volume to go all the way down whenever you open Google Meet or maybe your notification and ring volume to bump up during the workday but then drop back down in the evenings.

PRECISE VOLUME’S AUTOMATIONS OPEN THE DOOR TO ALL SORTS OF STEP-SAVING SMARTNESS.
Credit: JR RAPHAEL, IDG
The “Behavior” section within that same tab is where you can control the precise nuance level of your volume slider, if you want to make the control even finer than the default zero to 100 scale.

MAKE YOUR VOLUME CONTROL AS NUANCED AS YOU WANT WITH PRECISE VOLUME’S “STEPS” SETTING.
Credit: JR RAPHAEL, IDG
And the Equalizer tab at the bottom of the Precise Volume app is the place where — well, y’know. All that equalizer stuff, including the volume booster, resides.

IT MAY SOUND TECHNICAL, BUT PRECISE VOLUME’S EQUALIZER AREA IS FULL OF SIMPLE,
EFFECTIVE ENHANCEMENTS. Credit: JR RAPHAEL, IDG
And there ya have it: an awesome Android audio upgrade. The power is now at your fingertips, and a smarter, more efficient, and more powerful way of interacting with audio on your phone will always be present and waiting to be called into action.
source

 Recent Posts
Recent Posts